HaveIbeenPwned (HIBP) website has significantly expanded its database with hundreds of millions of newly compromised credentials extracted by hackers though infostealer logs
-
A large collection of compromised data, named ALIEN TXTBASE, has been added to the Have I Been Pwned (HIBP) database. The founder, Troy Hunt, explained that this data comes from people whose devices were infected with infostealer malware that steals personal information. This update includes 1. 5 terabytes of stolen credentials, which consists of 23 billion entries.
-
The analysis shows 493 million unique combinations of email addresses and websites, affecting 284 million individual email accounts. Additionally, 244 million new passwords have been added to the Pwned Passwords database, along with updated counts for 199 million existing passwords.
-
To improve access to this data, HIBP has launched new APIs aimed at helping organizations. These allow users to search the stealer logs by email and website domain, which assists in checking employee exposure and finding compromised customer credentials. These tools are part of a Pwned 5 subscription, which includes an API for email searches and a free web user interface for viewing email logs. A new "IsStealerLog" flag has been introduced to manage stealer log data differently.
-
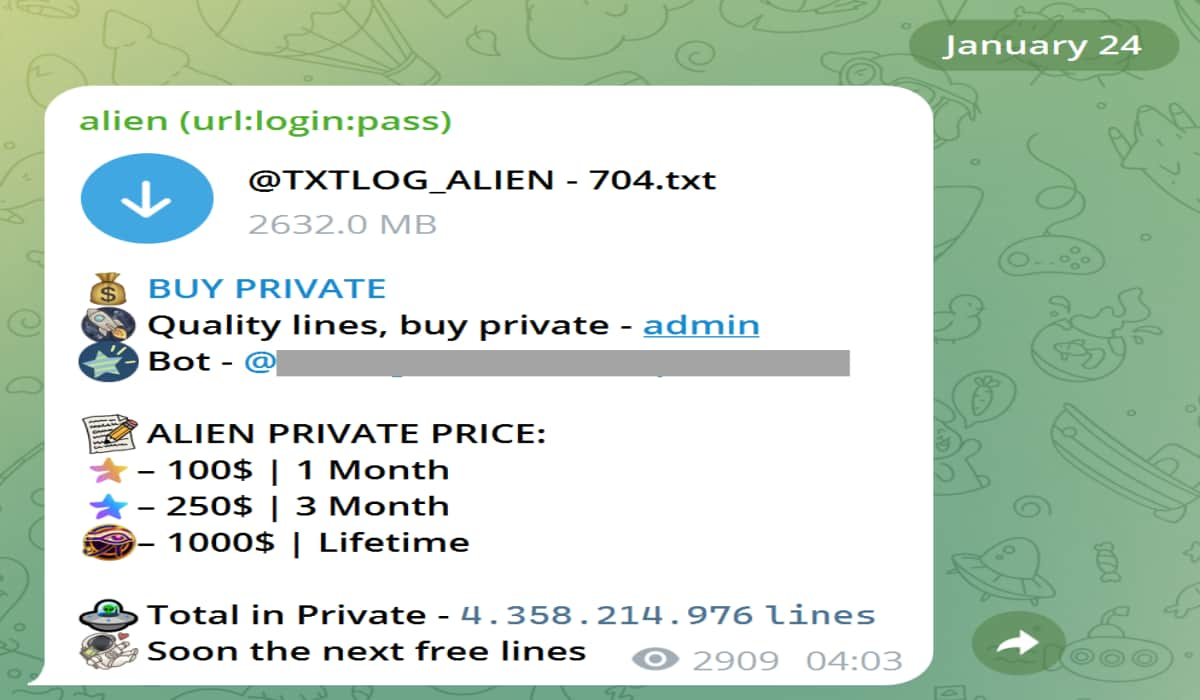
The data comes from a Telegram channel that distributed stolen credentials and was discovered after a government agency notified HIBP. The channel provides free samples and sells subscriptions to access more recently stolen data. The stolen credentials typically come from malware, often spread through pirated software or disguised downloads. Once a device is infected, the malware collects user credentials as they are entered online.
-
Unlike breaches from single sites, the ALIEN TXTBASE includes data from many sites, complicating verification. Standard methods to confirm data authenticity, like password resets, are challenging due to geo-fencing by services like Netflix. HIBP employs VPNs for verification and reached out to subscribers for confirmation. Although most data is genuine, it may contain false information, making it hard to tell what is valid. The ALIEN TXTBASE stealer logs are accessible through HIBP's existing search methods and new APIs, which help users identify compromised credentials. The free web UI for checking stealer log results by email is still available, and users can access it by visiting the notification page and verifying their email address.